
As institutional capital enters crypto, SOC 2 has become the baseline language of trust—proving that operational controls are documented, tested, and auditable. But while it validates process integrity, it wasn’t built for blockchain-specific risks like validator uptime, key management, or on-chain resilience. The next evolution pairs SOC 2 with ISO 27001 for continuous risk governance and DORA for regulatory resilience, creating a layered assurance model fit for digital assets. Looking ahead, a “SOC 3.0” paradigm will merge continuous monitoring, cryptographic proofs, and real-time transparency—turning trust from a static audit into a living, verifiable standard for institutional crypto infrastructure.
For digital-asset infrastructure, trust isn’t built on slogans, it’s built on standards. Among those, SOC 2 has become the universal language of operational credibility between crypto-native firms and institutional finance. Originally developed by the American Institute of Certified Public Accountants (AICPA), SOC 2 (System and Organization Controls) reports evaluate how well a company protects data across five “Trust Services Criteria”: Security, Availability, Processing Integrity, Confidentiality, and Privacy.
For traditional finance, SOC 2 has long been the standard for assessing whether vendors operate with robust security and governance. In the digital-asset economy, it now plays a similar role: bridging Web2 assurance frameworks and Web3 infrastructure. When an institutional investor, custodian, or exchange asks whether a staking provider or node operator is SOC 2-certified, they aren’t just checking the boxes, they want to understand reliability, transparency, and the ability to prove control in an environment where capital never sleeps.
The reason this conversation matters now is that the assurance landscape for crypto infrastructure is changing fast. In Europe, the Digital Operational Resilience Act (DORA) will begin enforcement in 2025, requiring continuous monitoring, incident classification, and third-party risk management for all critical ICT providers. At the same time, staking and custody firms across the U.S. and Asia are pursuing SOC 2 Type II and ISO 27001 certifications to meet procurement standards set by institutional allocators and banks. Together, these shifts are raising the bar: compliance is the price of admission to serve institutional capital.
But realistically, SOC 2 alone can’t capture every crypto-specific risk; key management, validator uptime, or smart-contract exposure all remain. But SOC 2 establishes a shared vocabulary of trust that both TradFi and DeFi understand. The challenge ahead, and the opportunity, is to extend that framework into the unique realities of blockchain infrastructure, to make assurance as continuous, transparent, and composable as the systems it governs.
SOC 2 is often described as the “gold standard” for operational assurance, and in many ways, it is. The framework, governed by the American Institute of Certified Public Accountants (AICPA), focuses on how an organization designs and operates its internal controls across five Trust Services Criteria:
These pillars reflect the essentials of trust in modern infrastructure, whether in a data center, a SaaS platform, or a staking service. For crypto and digital asset operators, SOC 2 shows that the organization has implemented, documented, and maintained security and operational processes with the same rigor expected in traditional financial institutions.
There are two key forms of SOC 2 reports:
For institutional partners, the distinction matters. A Type II audit provides evidence not just of policy, but of consistent execution, something risk teams view as critical for ongoing relationships.
However, SOC 2 has a well-defined boundary: it tests control integrity, not resilience or industry-specific adequacy. Organizations define their own controls, and auditors assess whether those controls exist and function as described, not whether they meet a universal security baseline. For example:
This is why SOC 2 is best understood as an attestation of operational maturity, not a certification of invulnerability. It provides essential assurance that controls are in place and working, the minimum entry requirement for institutional trust, but it stops short of enforcing resilience, continuity, or sector-specific standards.
For that reason, leading firms layer SOC 2 alongside frameworks such as ISO 27001, which prescribes a full Information Security Management System (ISMS), and DORA, the EU’s new Digital Operational Resilience Act, which mandates continuous incident reporting, stress testing, and third-party risk oversight for financial entities. Together, these frameworks cover what SOC 2 starts: SOC 2 establishes trust in process, ISO 27001 embeds continuous improvement, and DORA enforces regulatory resilience.
In short:
SOC 2 is the starting line for institutional trust. To turn attestation into resilience, firms pair SOC 2 with ISO 27001 and, in the EU, DORA
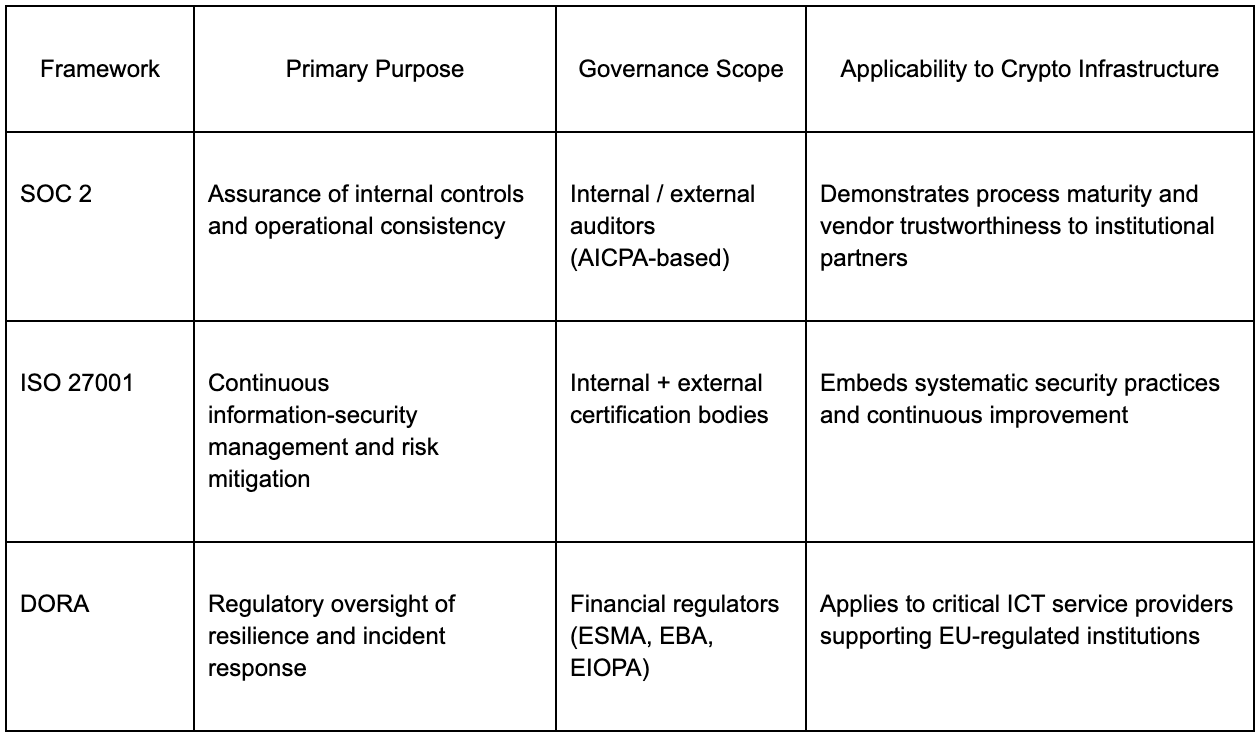
In traditional finance, governance frameworks tend to overlap, one defines how you manage risk, another defines what you must protect, and another defines how resilient you must be. In crypto infrastructure, that overlap is starting to take the same form. SOC 2, ISO 27001, and the EU’s Digital Operational Resilience Act (DORA) each play distinct but complementary roles in building institutional-grade security and assurance.
SOC 2 is fundamentally about trust through documentation and execution. It validates that an organization’s internal controls exist, are logically designed, and operate effectively over time. This is why it’s often the first certification sought by digital-asset custodians, staking operators, and exchange infrastructure providers entering institutional partnerships. SOC 2 is non-prescriptive, it doesn’t tell firms which encryption method to use or how to design access control, but it ensures that whatever control framework the company adopts is consistently applied and auditable.
Where SOC 2 stops at control attestation, ISO 27001 begins with systemic governance. Developed by the International Organization for Standardization, ISO 27001 defines a comprehensive Information Security Management System (ISMS), a living framework for assessing, mitigating, and improving security risks across people, processes, and technology. Unlike SOC 2’s periodic audits, ISO 27001 requires ongoing risk assessments, internal audits, and management reviews, embedding security into continuous operations. For institutions, this makes it the global benchmark for “security maturity.”
For crypto firms, particularly those offering infrastructure to regulated banks or funds, ISO 27001 complements SOC 2 by providing:
In practice, many institutions view SOC 2 + ISO 27001 as the combined standard for enterprise-grade crypto infrastructure: SOC 2 gives assurance to auditors and clients; ISO 27001 satisfies risk and compliance teams.
The Digital Operational Resilience Act (DORA), which will take effect across the EU in January 2025, represents the regulatory evolution of these voluntary frameworks. DORA explicitly targets financial entities and their critical ICT providers, imposing mandatory standards for:
Unlike SOC 2 or ISO 27001, DORA is law, not guidance, and its scope extends to critical service providers to regulated institutions. This means staking infrastructure companies, custodians, or blockchain node operators that serve EU-regulated banks may be classified as “critical ICT third parties,” bringing them under direct oversight by the European Supervisory Authorities (ESAs).
In other words:
SOC 2 earns trust.
ISO 27001 builds resilience.
DORA enforces both — under regulatory supervision.
For infrastructure providers like Chorus One, these frameworks work as a progression: SOC 2 establishes procedural trust, ISO 27001 embeds operational discipline, and DORA ensures resilience meets regulatory thresholds. Together, they create a compliance and assurance fabric that speaks both institutional and decentralized languages; aligning crypto infrastructure with the governance rigor expected in modern finance.
SOC 2 has become the passport for trust in digital-asset infrastructure, but it’s only the first chapter in what assurance must become for a 24/7, on-chain economy. The next phase will demand something closer to a “SOC 3.0” standard: one that integrates continuous monitoring, cryptographic verification, and regulatory transparency in real time.
Traditional SOC 2 audits are retrospective snapshots: a look back over six or twelve months to confirm that controls operated as designed. But blockchain infrastructure operates in real time, where validator uptime, MEV execution, or slashing incidents can occur in seconds.
Future assurance models will need to move from static attestations to continuous validation, using telemetry feeds, automated incident reporting, and live dashboards that update an organization’s control status dynamically. This shift mirrors the evolution of DORA’s continuous-resilience mandate and will ultimately bridge compliance with operational reality.
The next generation of assurance will combine conventional audits with on-chain verifiability. Concepts such as Proof-of-Control audits, cryptographic demonstrations that an entity controls validator keys or custody wallets without exposing them, and real-time attestations of uptime, governance participation, and key-management events could make trust both provable and programmable. In this “SOC 3.0” paradigm, auditors can verify it on-chain, linking SOC-style attestations to blockchain-based proofs that anyone can independently confirm.
For regulated institutions, this convergence will make frameworks like SOC 2, ISO 27001, and DORA interoperable.
For staking providers and validators, the benefits go beyond compliance. Real-time proof of validator performance, custody control, and incident transparency can enhance reputation, attract institutional delegations, and even feed into insurance underwriting and risk-weighted capital models.
That’s the future of assurance for crypto infrastructure: a living standard that blends the rigor of traditional compliance with the verifiability of blockchain itself. The path from SOC 2 to some new SOC 3.0 will be about designing trust that updates in real time.